
Cyberking Expert in Datacenter integration
Datacenter integration is a critical aspect of modern IT infrastructure, ensuring that all components work together seamlessly to support the organization's computing and data storage needs. If you have any specific questions or if there's anything specific you'd like to know or discuss regarding datacenter integration, feel free to ask, and I'll do my best to provide information or assistance.
Data Center Power Usage Efficiency Metric
Data Center PUE is a metric used to determine how efficiently your power is being utilized. A ratio of cooling power to IT power consumption. It is an important metric for those looking to save money, reduce carbon footprint, or increase server loads without increasing cooling capacity. The use of containment in your data center design has a massive impact on your PUE. Even a small computer room with a single rack can benefit from preventing hot and cold air mixing. This results in huge potential savings on energy costs. Try our PUE calculator to find out how much you can save.
Datacenter Proactive Monitoring
Proactive monitoring in a datacenter is a crucial practice to ensure the smooth and uninterrupted operation of critical IT infrastructure
Here are some key aspects of proactive monitoring in a datacenter:
Real-time Monitoring
Alerting and Notifications
Performance Metrics
Environmental Monitoring
Security Monitoring
Predictive Analysis
Automation
Historical Data Analysis
Compliance and Reporting
Implementing proactive monitoring in a datacenter requires the use of monitoring tools and software, as well as well-defined processes and procedures. It's an essential part of ensuring high availability, performance, and security in datacenter environments
if you are looking for a solution contact us for POC talk to an Expert




Datacenter integration solutions
Here are some key components of a datacenter integration solution:
Unified Management Software
Virtualization Technologies.
Storage Integration
Network Integration
Automation and Orchestration
Cloud Integration
Security Integration
Power and Cooling Management
Monitoring and Analytics
Compliance and Reporting
Backup and Disaster Recovery
Documentation and Documentation Management
Scalability and Future-Proofing
You may also want to consult with IT professionals or specialists in datacenter management to help design and implement a solution that best fits your needs
Datacenter physical security
Here are some key components of datacenter physical security:
Access Control
Perimeter Security
Security Cameras and Surveillance
Intrusion Detection Systems (IDS)
Security Guards
Biometric Access Control
Mantraps
Cabinet and Rack Locks
Environmental Controls
Power and Data Cabling Security
Visitor Logs and Badges
Secure Loading Docks
Secure Storage for Backup Media
Training and Awareness
Datacenter physical security should be considered as part of a comprehensive security strategy that also includes cybersecurity measures to protect against digital threats. Combining both physical and cybersecurity safeguards helps ensure the integrity and availability of datacenter operations.
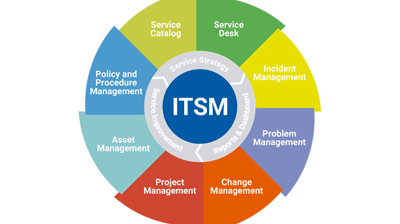
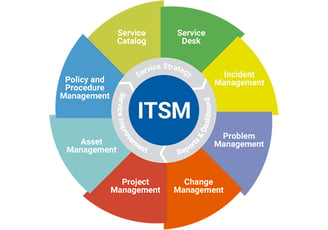
Datacenter ITSM
Here are some key aspects of Datacenter ITSM
Service Catalog
Incident Management
Configuration Management
Problem Management
Asset Management
Service Level Management
Capacity and Performance Management
Security and Compliance
Automation
Reporting and Analytics
By adopting Datacenter ITSM principles and implementing the appropriate tools and processes, organizations can improve the reliability, efficiency, and responsiveness of their datacenter operations, which is essential for supporting the broader IT needs of the organization.




ISO 27001 for Datacenter
an Information Security Management System (ISMS). An ISMS is a systematic and structured approach to managing and protecting sensitive information within an organization. Here are the key aspects of ISO 27001 ISMS:
Scope and Objectives
Risk Assessment
Risk Treatment
Information Security Policy
Roles and Responsibilities
Asset Inventory
Security Controls
Incident Response Plan
Monitoring and Measurement
Documentation and Records
Continuous Improvement
Certification and Compliance
ISO 27001 is a flexible standard that can be adapted to the specific needs of your organization. It provides a structured framework for managing information security, which is crucial in today's digital age when data breaches and cyber threats are on the rise. By implementing ISO 27001, organizations can demonstrate their commitment to protecting sensitive information and maintaining the trust of their stakeholders.
